Cyber Threat Intelligence Storing and Sharing
The IRIS project aims to assist European CERTs/CSIRTs minimise the impact of cybersecurity and privacy risks, as well as threats introduced by cyber-physical vulnerabilities in IoT platforms and by adversarial attacks on AI provisions and their learning/decision-making algorithms. To this end, IRIS aims to integrate and demonstrate a platform addressed mainly to CERTs/CSIRTs for assessing, detecting, responding to, and sharing information regarding threats and vulnerabilities of IoT and AI-driven ICT systems. The IRIS platform will be demonstrated and validated in three realistic environments with the engagement of three smart cities (Helsinki, Tallinn, and Barcelona), along with the involvement of national CERTs/CSIRTs and cybersecurity authorities.
Within the IRIS platform, particular emphasis is given to the Cyber Threat Intelligence (CTI) module which enables (through its submodules) the collection, storage, correlation, and sharing of information about threats and vulnerabilities from both internal and external sources. Internal sources comprise honeypot instances, firewalls, SIEM, IDSs etc.; these are selected from the IoT and AI-based infrastructures and are configured in order to ensure optimal results in terms of the quality of information. This kind of information can be used to extract knowledge regarding attackers and any other abnormal behaviour. External sources include among others vulnerability databases, CERT feeds, databases with Proof-of-Concept (PoC) exploits, social media platforms, as well as various sources from both Surface and Dark Web. The CTI module provides a convenient and effective functionality which enables the gathering of cybersecurity information from internal and external sources concerning IoT and AI-driven ICT systems.
After completing the collection process, CTI is extracted using rule-based and machine learning-based analysis techniques. For example, machine learning techniques, such as pattern identification and analysis and anomaly detection, can extract valuable CTI from the collected data. Data collected from external sources follow a semi-structured or unstructured format and therefore regular expressions and heuristic approaches can be used to transform the data into an appropriate structured format that would allow for their analysis. On the other hand, information collected from internal sources already follows a structured format.
Following the identification of sources, the information gathering, and the CTI extraction processes from internal and external sources, one more critical step is the CTI enrichment based on correlation techniques; in this case, rule-based and machine learning-based correlations are used.
Overall, the main functionalities of the CTI module are:
- Automatic collection of information concerning cybersecurity threats and vulnerabilities from internal sources;
- Automatic collection of information concerning cybersecurity threats and vulnerabilities from external sources such as US-CERT, EU-CERT, etc.;
- Effortless incorporation of new sources of interest;
- Automatic extraction of CTI; and
- Implementation of simple and advanced correlation techniques in order to enrich the extracted CTI.
The enriched CTI is stored in the Cyber Threat Intelligence Sharing component which is based on the MISP platform and corresponds to a platform for storing and disseminating CTI in a secure and efficient manner, both manually and automatically.
The procedure of sharing is critical as it enables different interested parties (CERTs, CIRTs etc.) to be informed in a timely manner about the cyberattack landscape. Various tools or platforms exist that facilitate the sharing of CTI information, such as OpenCTI[1], MISP[2], and GOSINT[3]. The MISP platform has gained popularity among cybersecurity professionals, CERTs, CSIRTs, and the MeliCERTes ecosystem as MISP is part of it. This is useful as it can depict semantic information of various data generated over time. Information visualisations and keyword-based search capabilities are also essential characteristics of the MISP platform.
In particular, the CTI sharing component provides a user-friendly dashboard that the user can use to interact with the stored CTI and perform various actions, such as writing or modifying data. Furthermore, it leverages the MISP API to allow sharing and further processing of the stored data by components developed in various programming languages (including Java and Python).
Overall, the main functionalities of the CTI sharing component are:
- Correlation and enrichment of the collected CTI;
- Classification of gathered CTI according to the needs of the end-users;
- Storing and sharing of CTI; and
- Provision of a user-friendly environment of trust for sharing CTI.
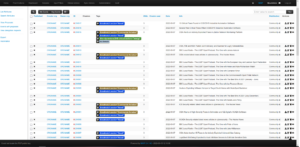
Figure 1: Cyber Threat Intelligence Sharing MISP UI
To contextualise the collected information, instead of simply storing them in MISP, the appropriate MISP data objects are used and upgraded when needed.
In summary, the CTI module developed within the context of IRIS provides different functionalities consisting of the following distinct phases: (1) collection of information from internal and external sources, (2) CTI extraction from the collected data using both rule-based and machine learning-based analysis techniques, (3) enrichment of the data using correlation techniques, and (4) sharing of CTI information to the interested parties using a user-friendly dashboard in order to inform them in an effective, efficient, and timely manner about the cyber threats landscape.
[1] https://github.com/OpenCTI-Platform/opencti
[2] https://www.misp-project.org/
[3] https://github.com/ciscocsirt/GOSINT







