Autonomous Risk-based Response & Self-Recovery
Uptake of IoT and AI driven ICT systems in Europe is crucial for our common future, but it is dependent on our strategic ability to protect these systems from cyber threats and attacks. Due to the innate complexity of hyper-connectivity between different IoT systems and the black-box nature of most advanced AI systems, interpreting misbehaviour during the configuration, or run-time operation of the ICT systems depending on them is uniquely challenging [1], [2]. To address this challenge and mitigate cybersecurity incidents in IoT and AI-driven ICT infrastructures, systems and applications, IRIS delivers a collaborative-first approach centred around CERTs/CSIRTs incorporating a threat intelligence-driven toolkit for autonomous incident response and recovery.
Tools for autonomous incident response and recovery have been around for several years [3]. Autonomous response pertains to the ability to execute automated mitigating actions considering attack detection. Self-recovery describes a system’s degree of cyber resilience for remediating ongoing compromise and facilitating a return to normal security behaviour. Both concepts have gained considerable attention due to recent technology platform innovations in the threat response workflow and automated orchestration. The concept of Security Orchestration Automation and Response (SOAR) has emerged as a promising framework for implementing a symbiotic stack of interoperable security platforms for collecting, analysing, prioritising, and performing analytically consistent actions and response procedures for security data from multiple sources without the requirement for human assistance. This advancement in autonomy has optimised response and recovery of compromised systems by reducing the time required to implement mitigation activities by programmable middleware platforms. However, existing SOAR technologies are currently static with respect to response logic and lack self-recovery procedures that do not rely on human operators’ intervention.
Within IRIS, we aim leveraging dynamic game-theoretic algorithms as an autonomous optimisation technique for determining the best course of action against identified threats. Risk-based response was first introduced in 2018 as a methodology for autonomous containment of compromised systems [4]. IRIS’s risk-based response processes will integrate with existing orchestration capabilities for assessing risk in real-time, whether indicators of compromise are received by attack detections of threat intelligence data sources. The risk-based response optimisation will develop autonomous modelling criteria for assessing the impact of attack vectors and self-recovery interventions. In the case of IoT infrastructure and AI-provision self-recovery, this may be determined as an optimal recovery action facilitating the preparation of less disruptive system remediation or failover activation. This is a significant innovation in the domain of cybersecurity response for IoT and AI-provisioned infrastructure and recovery in the sense that it proposes an intelligent risk-based criterion as a coordinating aspect of self-recovery for the greater cyber resilience of a system. Alongside the IRIS threat intelligence companion orchestrator workflow manager, the risk-based response and self-recovery module builds upon innovations in SOAR and threat intelligence execution by providing an intuitive and programmable API for CSIRT/CERT analysts to define risk parameters and modes of self-recovery for a system’s infrastructure and services.
Figure 1 shows a high-level architecture of the risk-based response and self-recovery. The module will be released on November 2023 and will be validated in the context of the IRIS pilots during 2024.
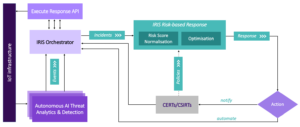
Figure 1 – IRIS’s risk-based response & self-recovery module
References:
[1] ENISA Report (2017). Baseline Security Recommendations for IoT.
[2] ENISA Report (2020). Artificial Intelligence Cybersecurity Challenges.
[3] Donevski, M., & Zia, T. (2018). A survey of anomaly and automation from a cybersecurity perspective. In 2018 IEEE Globecom Workshops, pp. 1-6.
[4] Mohammad, S. M., & Surya, L. (2018). Security Automation in Information Technology. International Journal of Creative Research Thoughts (IJCRT), Volume 6.







