As explained by our partners in previous blog posts, the platform that is being developed at the IRIS project will be deployed and validated with the help of 3 Pilot Use Cases (PUC), located in 3 Smart Cities: Barcelona, Tallinn and Helsinki. Validation is a very necessary step to guarantee that the requirements and needs set by the project stakeholders and end user communities are satisfied. In this blog post we will focus on the PUC1, where the IRIS platform will be used to monitor an IoT system deployed at the tramway station in Barcelona.
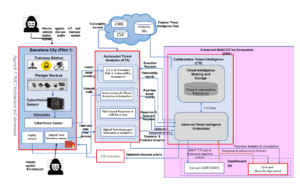
After the final version of the architecture has been released in M18 (February 2023), we are ready to begin the process of validation. The IRIS components that will be tested in this PUC are the Automated Threat Analytics (ATA) and the Enhanced MeliCERTes Ecosystem (EME) modules, each one of them comprised of the following tools:
Automated Threat Analytics
- IoT & AI-Provision Risk & Vulnerability Assessment: Performs scans against the network infrastructure and devices on demand or automatically, reporting vulnerabilities found on the components or their communications, among others.
- Autonomous AI Threat Analytics & Detection: Receives the traffic generated on the network and correlates it with the use of an AI system, in order to detect attacks performed by malicious agents.
- Risk-based Response & Self-Recovery [1]: Receives requests from the Intelligence Orchestrator and generates optimized, risk-based responses, which can then be executed automatically, thus effectively and quickly blocking an intruder.
- Digital Twin Honeypot Telemetry & Analytics [2]: Consists of a clone of the infrastructure, made to trick attackers into believing the system is legitimate, and allowing the discovery of risk exposures.
Enhanced MeliCERTes Ecosystem
- Collaborative Threat Intelligence: Acts as a medium of communication between external data sources and stakeholders and among IRIS components.
The validation of the Barcelona use case will focus on IoT infrastructure, which means that attacks not commonly found on IT systems will have to be taken into account. This includes attacks such as physical tampering or sensor communication spoofing and sniffing.
For the physical part, we will emulate an attacker going into the tramway station and removing, adding or replacing devices such as cameras, environmental sensors or malicious devices, with the intention of disrupting the service by blocking or sending fake data, or getting access to the IoT network.
Besides, we will simulate being an attacker, connecting both from the tramway station or with access to the IRIS network, and we will follow the common procedures for gaining unauthorized access to a system, which will include network reconnaissance, brute forcing passwords of different interfaces or machines, running a Denial of Service attack, and much more.
Finally, we will verify that each component of the platform to be tested in this pilot use case generates the expected alert for every action executed.
References:







